How to add Azure Active Directory authentication for Azure function app
In this article, We are going to explain how to authenticate Azure Function Apps with Azure Active Directory Authentication. As we know, in serverless architecture, the users only write the business logic code, and all other worries are taken care of by the cloud provider. This helps businesses to quickly implement solutions and ship it to customers with more quality. Also, another important point about serverless applications is that they are scalable on-demand, which means as a developer, we no longer need to monitor or manually pull up the resources when the executions are more.
Prerequisites
There are a few prerequisites that we must be fulfilled before having Azure Active Directory Authentication to Azure Function App. These are as follows:
- A valid Azure account with a subscription.
- A Service Plan within which the function is to be created and executed. Usually, there are two types of service plans, App Service Plan and Consumption Service Plan. App Service Plan allows the user to continuously run the code on a virtual machine that is defined by the user, whereas the Consumption Service Plan bills only for the duration of which the function runs. There is also a timeout set, which is, by default, set to 5 minutes for these functions.
- A Storage Account in Azure, which will be linked to the Function App and can be used to store information such as logging and managing triggers, etc. We can also use this storage account to store the configuration files for this function and pushing output from function to queues , tables and blobs.
Creating an Azure Function
There are many ways in which we can create a Function app:
- Azure Portal (https://portal.azure.com)
- Azure CLI/Powershell
- Using Code Editor like Visual Studio
- Search for Function App under Compute.
In this Article, We will go with first option. (Azure Portal) for Creating an Azure function App.
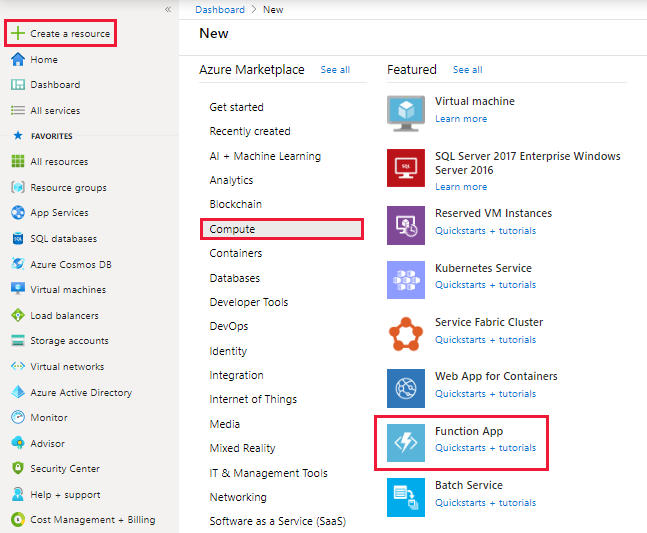
2. Follow the on screen instruction and fill out the fields accordingly. In this article, I am using powershell core as Function App platform.
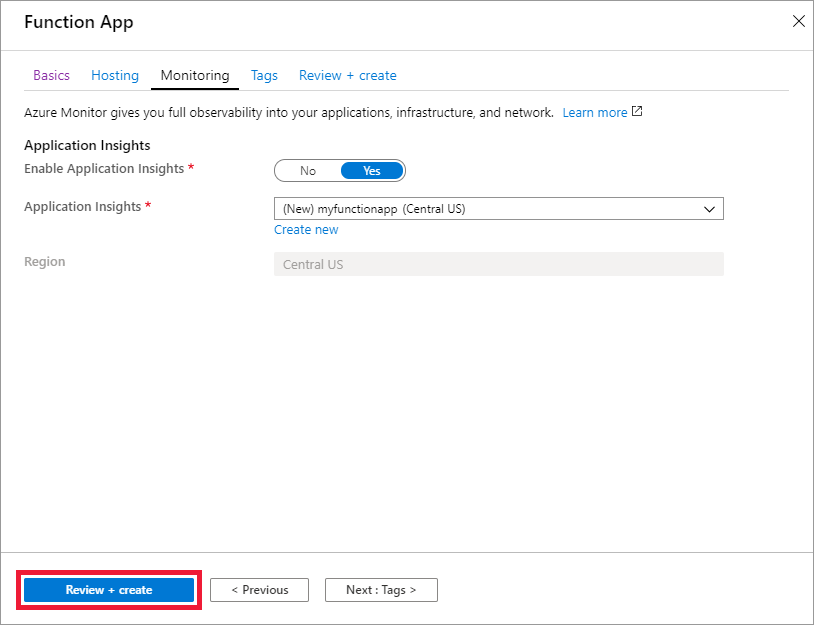
It may take 2-3 minutes to deploy the function app.
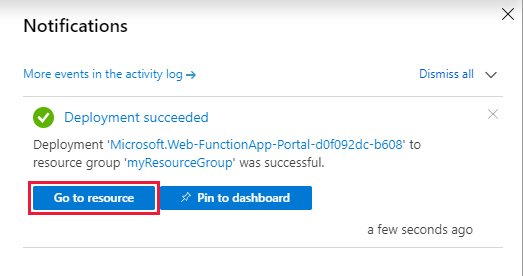
Now, We have Azure Function app in place. We can add new function to it. In this case, we are going to choose a HTTP trigger, as shown in the screenshot below. We choose to use a HTTP trigger function because later we will show only authenticated users can get the results when sending a POST request to this function.
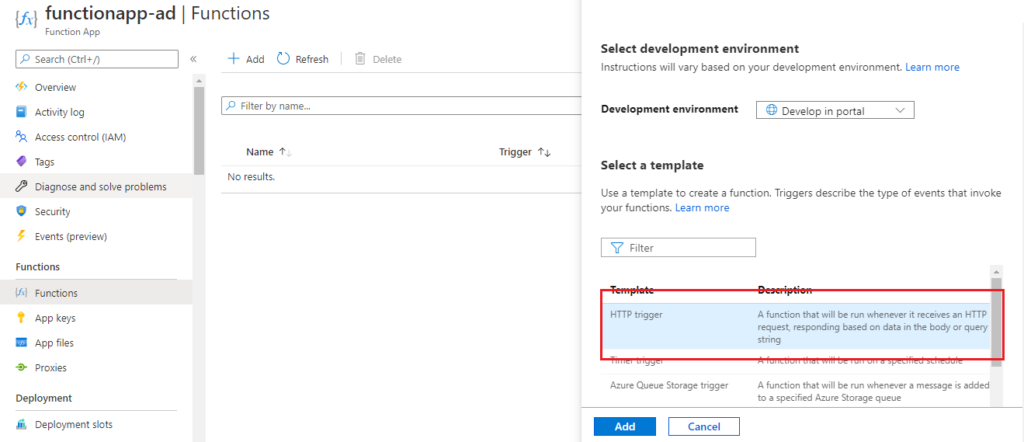
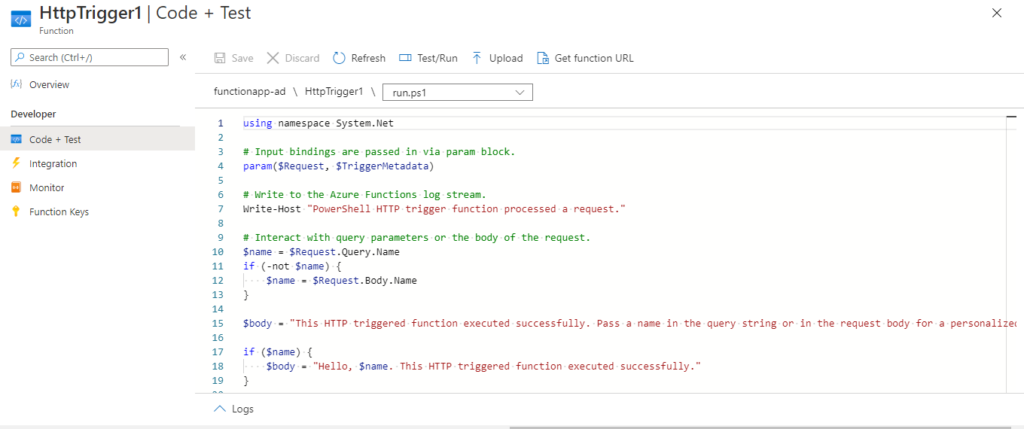
Now we have a Sample HTTP trigger function for our function app as shown in below screenshot.
By default only GET and POST request are enabled on the function. We can add or remove request methods in Integration tab under Function as shown in below screenshot.
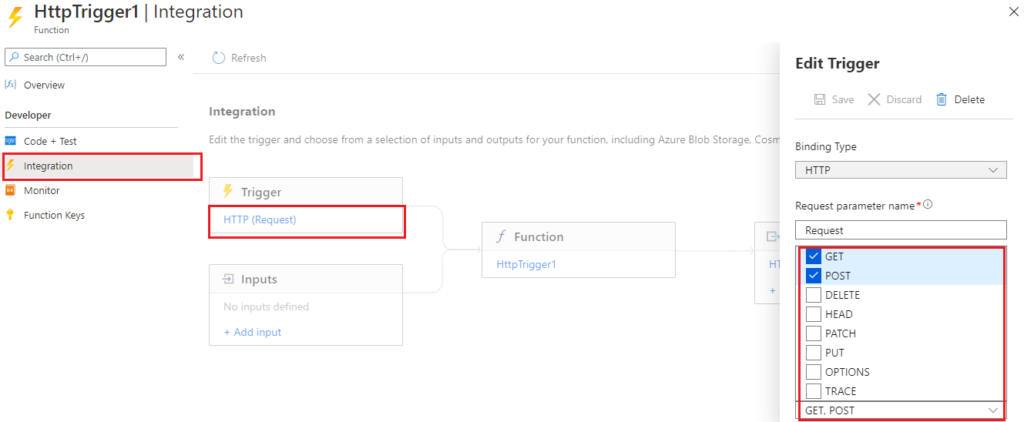
You can add any request method available. I am going to use POST method only for sending HTTP request.
Lets test it without Authentication. Click on Test/Run at the top pane of HTTP Trigger Function in Azure portal.
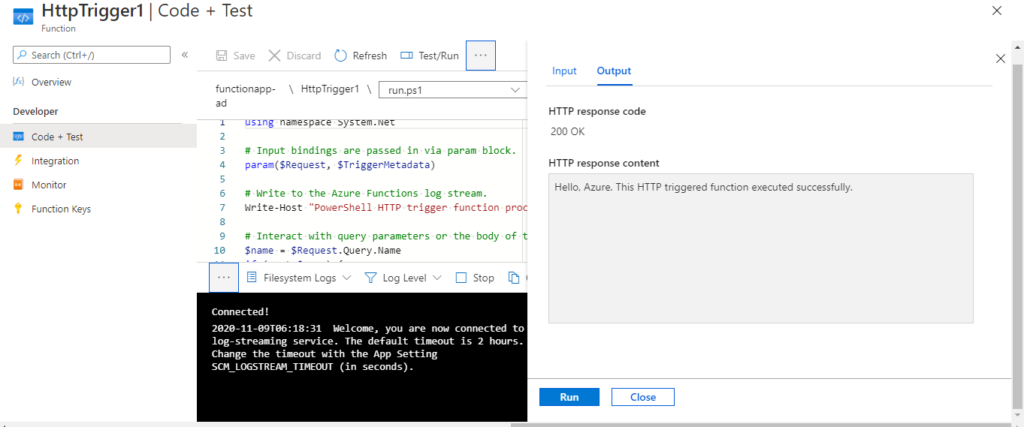
Lets setup the Azure Active Directory for the function app now.
- Create an Azure AD application. Go to Active Directory > App Registration > New Registration
- Enter Name of Active Directory Application.
- Copy the Function App URL for the function app and append it with "/.auth/login/aad/callback" and paste that into Redirect URI.
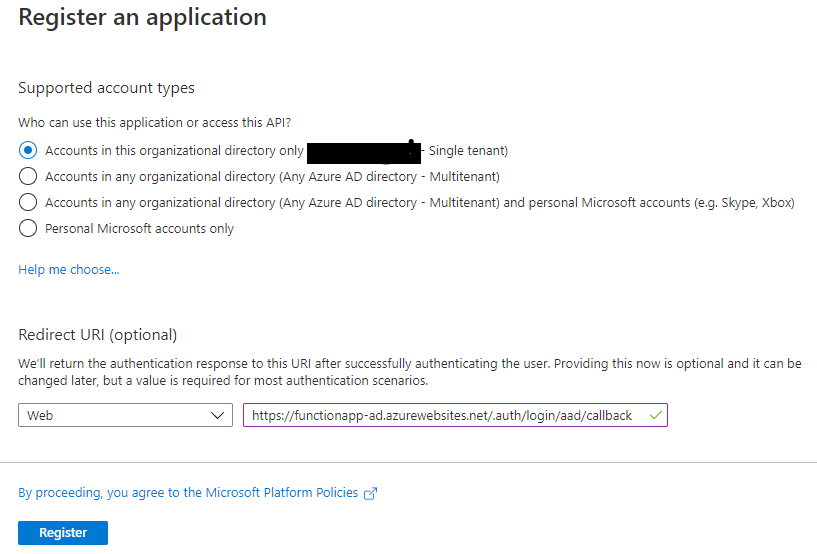
4. Register the Azure AD application.
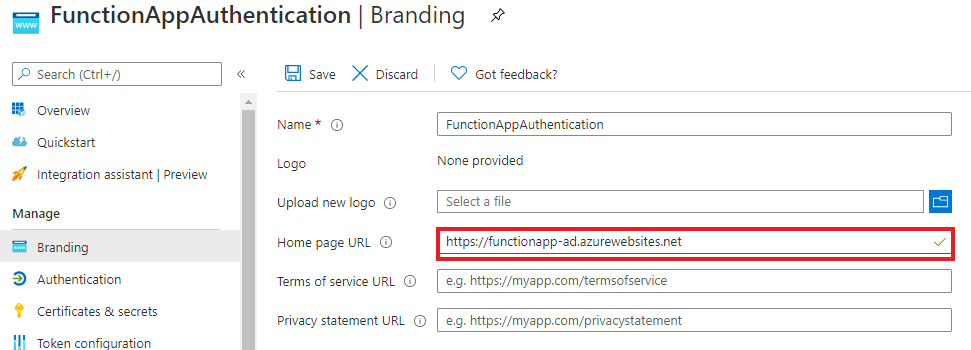
5. Now we have Azure Active Directory application ready. Click on Branding under Manage and change the Homepage URL to function app URL.
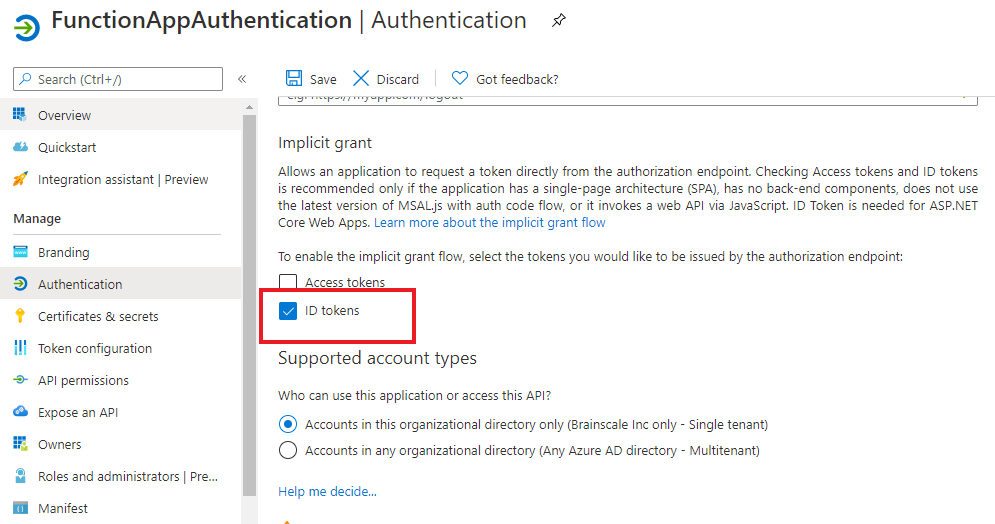
6. Go to Authentication and check the ID tokens checkbox for enabling issuing the tokens for implicit grant by authorization endpoint.
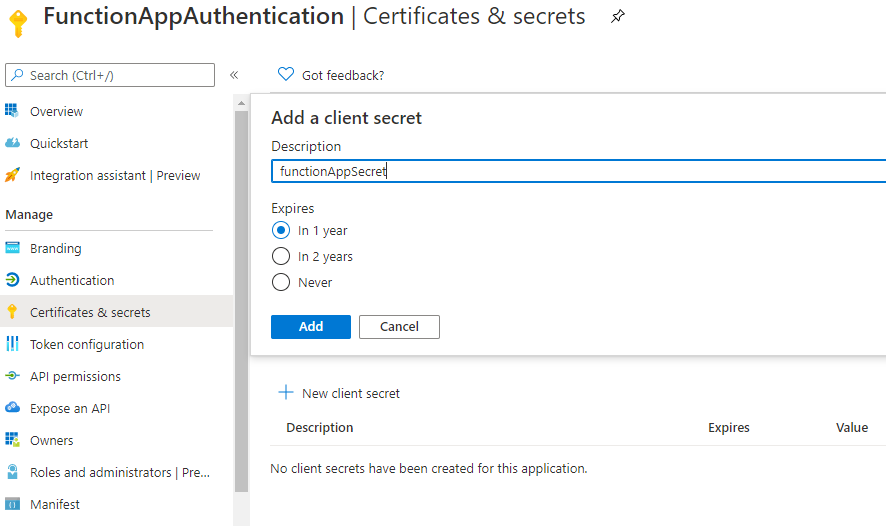
7. Click on Certificates & Secrets and create a client secret for Azure Active Directory Authentication and save it in a secure place as it can not be retrieved again.
8. Click on Expose an API and set the Application URI to function app URL.
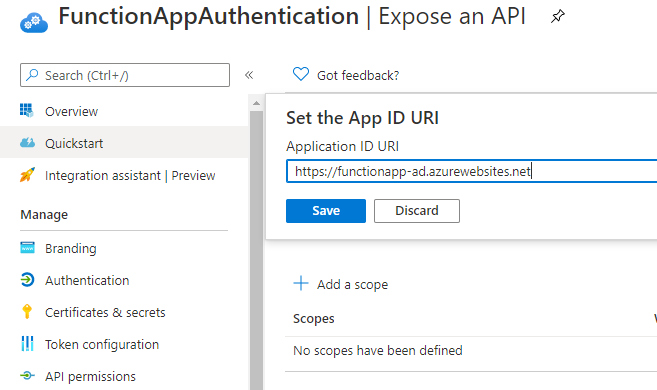
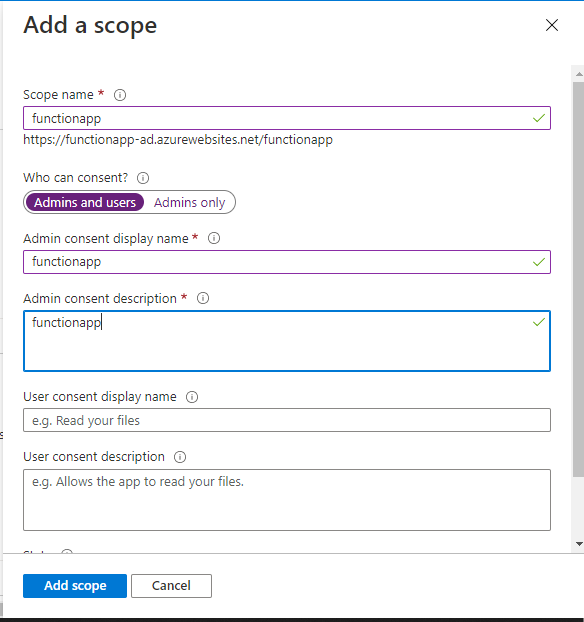
9. Define custom scopes to restrict access to data and functionality protected by the API. An application that requires access to parts of this API can request that a user or admin consent to one or more of these.
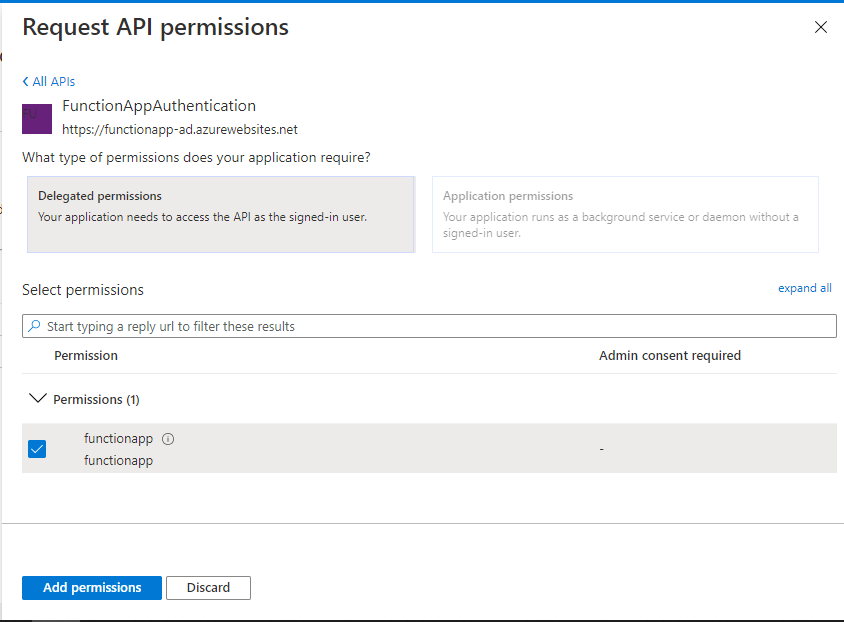
10. Under API permissions, Add a delegated permissions for the scope created for Azure function app.
Permissions on Azure AD application are all set now. Lets configure the Azure function app to use AD authentication.
11. Click on Authentication/Authorization.
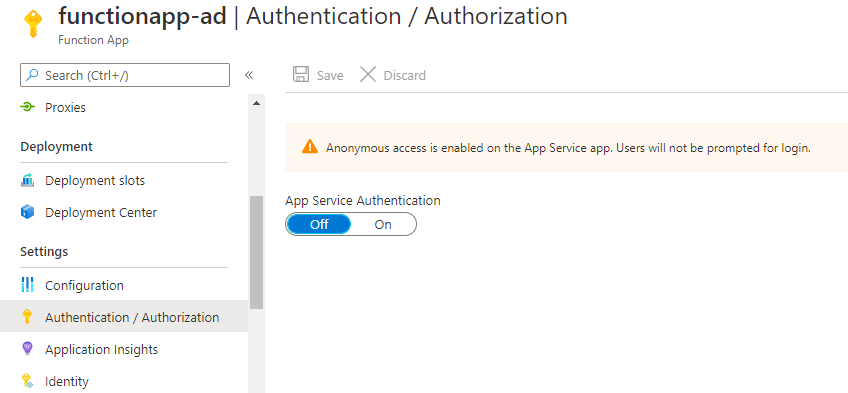
12. Set the App service Authentication to ON and click on Azure Active Directory under Authentication Providers.
13. Select the Management Mode to Advanced and fill in the required details.
Following details are needed.
- Service Principle client ID.
- Service Principle Client Secret.
- Issuer URL
Copy the details for Azure AD application created and fill in the required details.
Issuer URL would be : https://login.microsoftonline.com/<TENANT_ID>/
Make sure the trailing '/' is there in Issuer URL.
Under Allowed Audiences, Allow the following URLs.
https://<FUNCTIONAPPNAME>.azurewebsites.net
https://<FUNCTIONAPPNAME>.azurewebsites.net/.auth/login/aad/callback
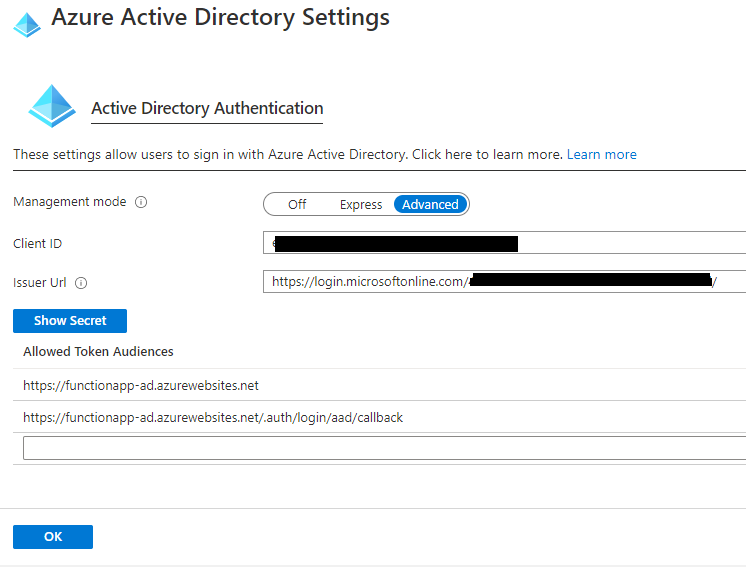
Click OK and change the "Action to take when request is not authenticated" to "Log in with Azure Active Directory" and Save.
We are all set now for Azure AD authentication for Azure function app.
Lets test it out now. I will be using the POSTMAN for sending the POST request to function app.
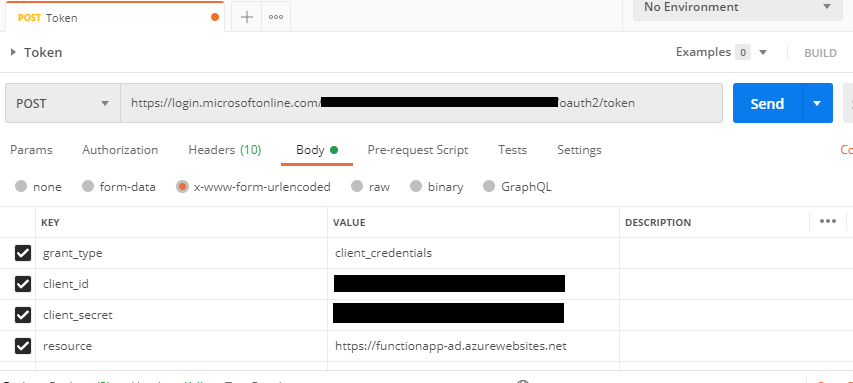
- Lets get a token first to send request to run function in azure function app.
Following things are required in order to get the token for running function app.
- Client ID
- Client Secret
- Function app URL
- Tenant ID
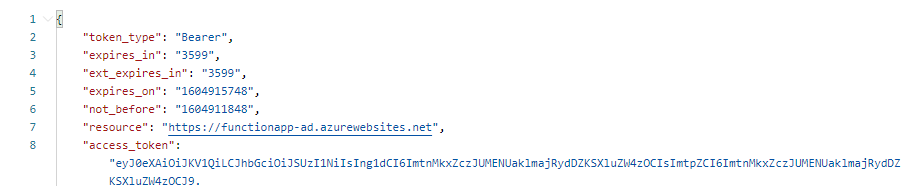
Output would give you a access token that you can use to run function in Azure function app.
Now, we will run our Azure function and will pass the token we got from above API call.
We will copy the function URL and will send a POST request to check if it is successfully authenticated to Azure Active Directory.

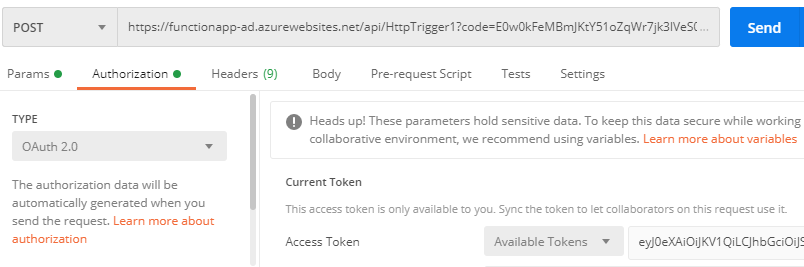
We will run the HTTP request now. You should now see the ouput which looks like what is shown in the following screenshot.
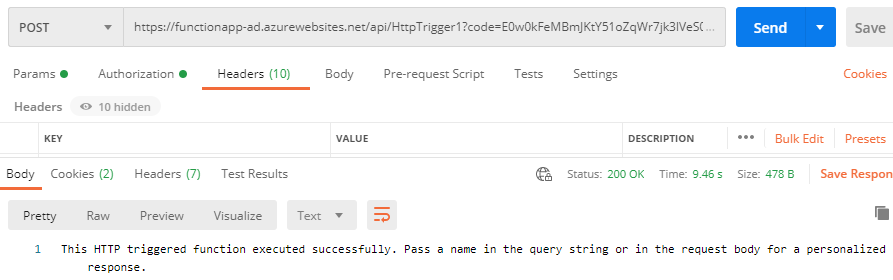
We have successfully authenticated to Azure Active Directory for Azure function.That’s all it takes to setup a simple authentication for Azure Function with Azure AD. Thanks!
Thanks for Reading...!!!!!